In this tutorial, we will learn about what is IAM identity provider and federation and how to add an Identity provider. Amazon IAM is a web service which is used to securely access all AWS resources. It controls the permission of all the users accessing any AWS resources. Authorization and Authentication of a user is completely managed and controlled by IAM service.

What is IAM Identity Provider and Federation
IAM Identity provider (IdP) is used to establishe a trust relationship between your aws account and the IdP by creating an IdP entity which we will see later in this tutorial. There are two types of IdP supported in AWS.
- SAML (Security Assertion Markup Language)
- OpenID Connect (Web identity federation)
SAML is use to authenticate providers like Shibboleth. OpenID Connect is use to authenticate users like Google, Facebook etc. IAM only supports providers which are compatible with either of two mentioned IdP in AWS. In this tutorial, we will see how we can add an OpenID Connect provider to access the AWS resources but first let’s understand why OpenID Connect providers are required.
Let’s understand OpenID Connect provider with an example . Suppose you have created a mobile application which requires access to few AWS resource like S3 or any database services to store the application data. To use any AWS service, you first have to authenticate yourself by signing in using AWS access Key. This authentication will be required every time you use the AWS services. Hence, credentials has to be embedded in your application.
It is never recommended to embed credentials in such applications, which large group of people will install in their devices. Instead, application should be developed in such a way that user requests for a temporary credentials when needed using Web identity federation. Any provider compatible with OpenID Connect can sign in using any external IdP like Facebook, Salesforce, Google etc. In this method, user receives an authentication token which is exchanged to get the temporary security credential in AWS. This token is internally mapped to a role with permissions to access the AWS resources. In this way, identity provider makes your AWS account safe and secure.
How to Add an Identity Provider using 5 Easy Steps
Also read: How to create EKS cluster
Now that we have understood what an Identity provider is and why we use it. Let’s now add one OpenID provider by following below steps.
Prerequisite
- An existing EKS cluster
- OIDC(Open ID Connect) url of your cluster
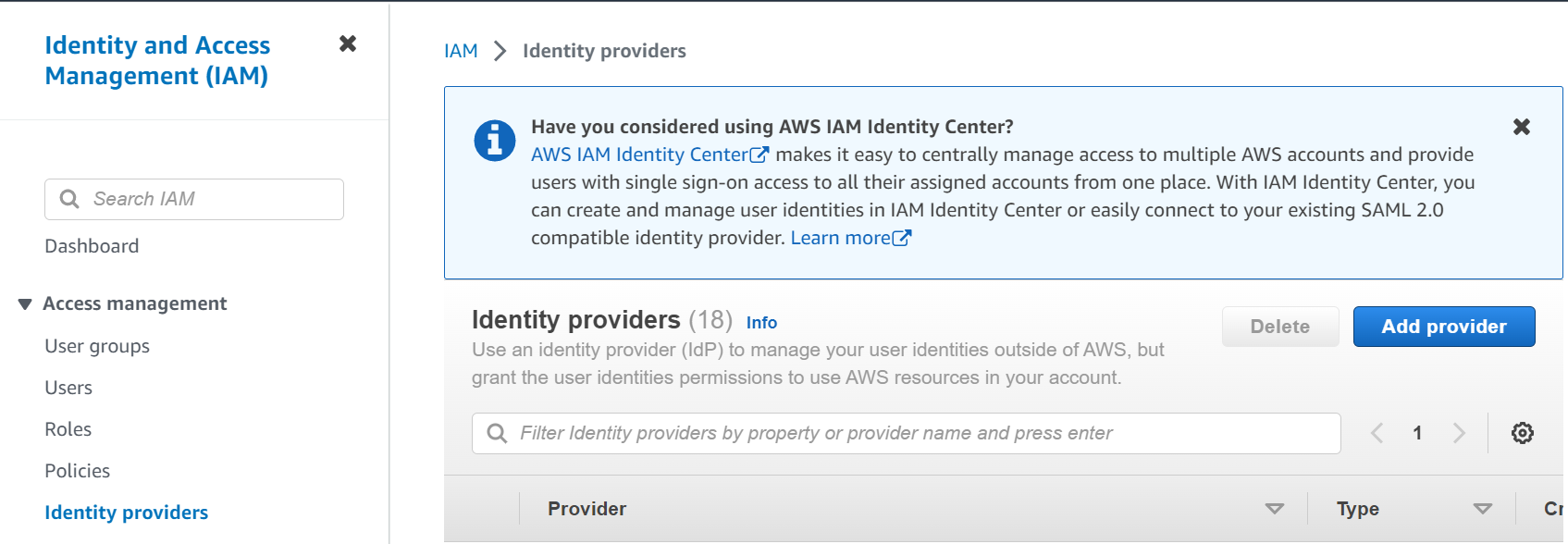
Step-1: Search Identity Provider
In this step, Click on IAM service and then click on Identity providers from the left panel. Next, click on Add provider.
Step-2: Get URL of IdP
In this step, connect to your EKS cluster and use below command to get your cluster’s IdP URL. Here <region-code> will be the region where your cluster is created and <cluster-OIDC-provide-id> will be your cluster’s OIDC provider id.
[nasauser@linuxnasa~]$ aws eks describe-cluster --name <cluster-name> --query "cluster.identity.oidc.issuer" --output text https://oidc.eks.<region-code>.amazonaws.com/id/<cluster-OIDC-provide-id>
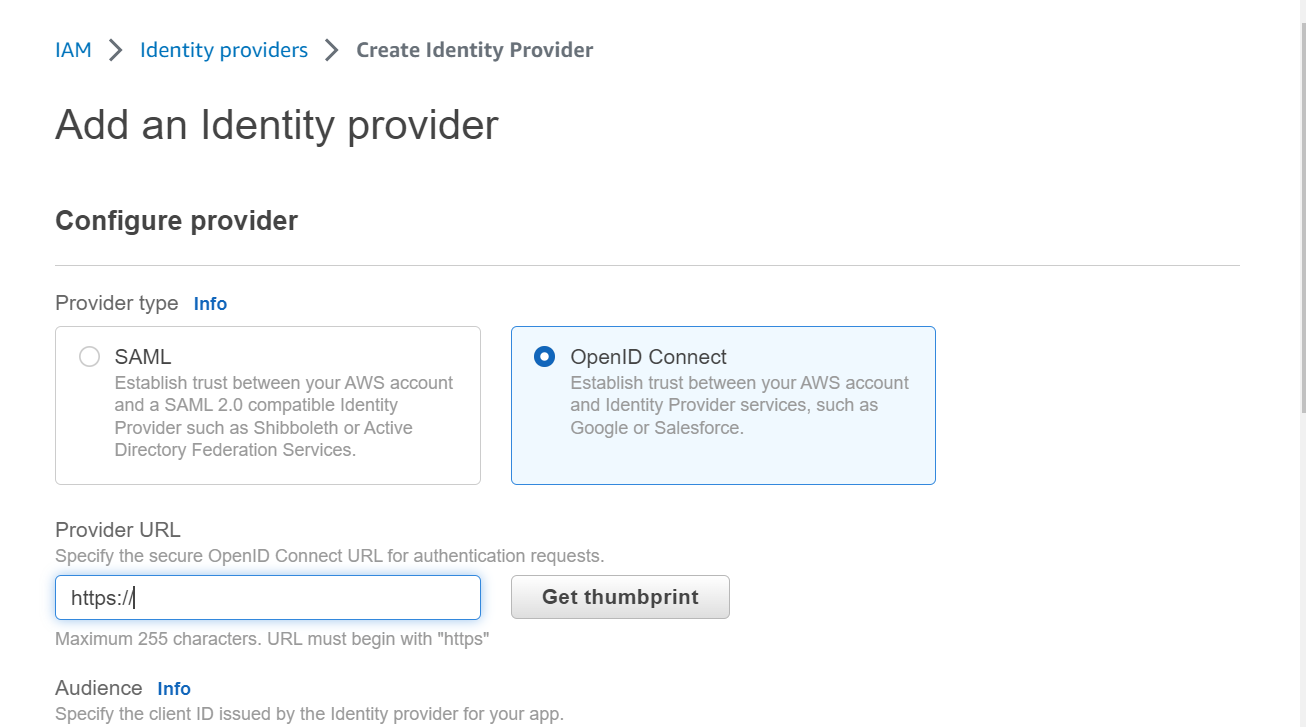
Step-3: Add IdP URL
In this step, select OpenID Connect as provider type. Next, copy the provider url from above step and paste under Provider URL. After providing the URL, click on Get thumbprint which is used to verify the server certificate of identity provider.
NOTE:
Provider URL
- Must be unique
- Must not use a port number
- Must start with https://
- Is case-sensitive
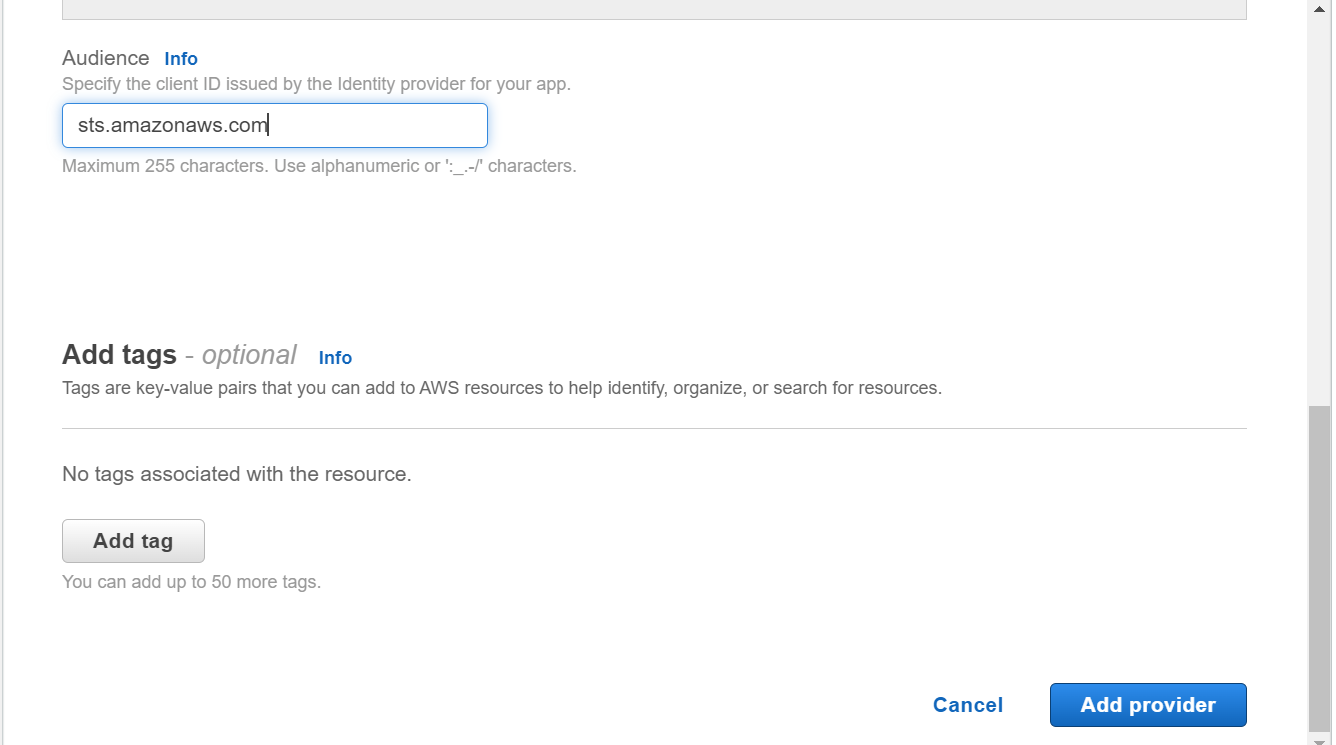
Step-4: Add Audience
In this step, add audience for your application. Audience also known as Client ID is received when you register your application with the IdP. In our case, we will use the client id sts.amazonaws.com.
Next, click on Add provider to add the provider.
Step-5: Verify Created IdP
In this step, if provider is added, a message will appear at top as shown below. Use find search option to select your identity provider. If your provided is listed, it is successfully added.
Conclusion
In this tutorial, we learnt about IAM Identity providers and federation and how we can add any provider in IAM. In order to use these providers, we have to create a role and add permissions( via policies) to it. You can read more about How to create IAM role to use external IdP.